HGAME 2023 week3 & week4 writeup
patchme
main 函数里有个 gets,同时翻了翻发现有一段代码,里面有个 mprotect 下面是对一个大数据段的异或操作,显然是个 SMC,一个比较 pwn 的方法是利用 get 的漏洞改汇编然后跑出 flag,也可以直接逆。
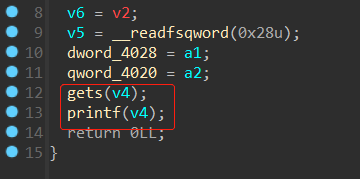
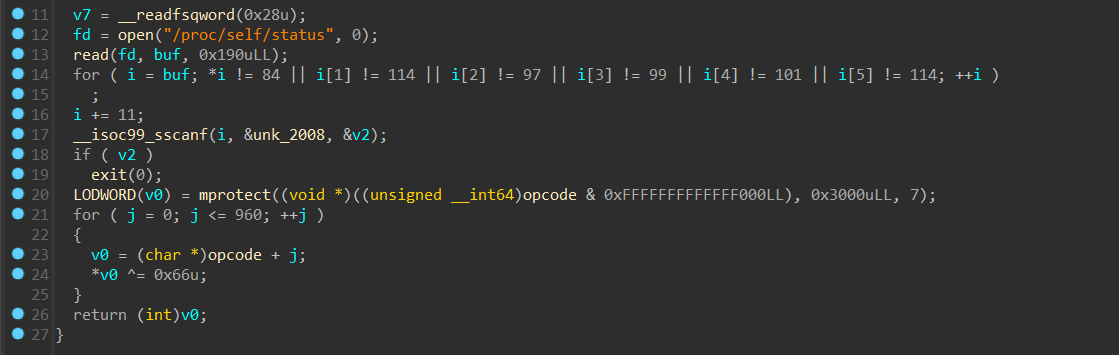
由于只是一个简单异或,考虑用 idapython 直接实现 smc 的解密
1 | from idc_bc695 import * |
解密完的数据 analyze 以后得到关键代码
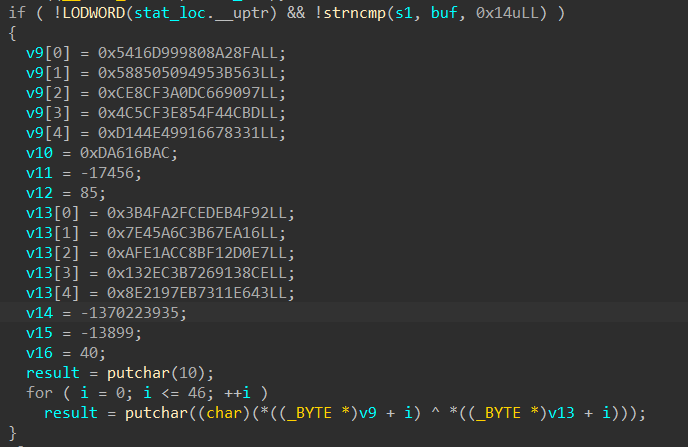
1 |
|
运行得到 hgame{You_4re_a_p@tch_master_0r_reverse_ma5ter}
kmusic
把 dll 文件扔进 exeinfo 里面发现是 .net 文件,用 dnspy64 打开,定位到 main 函数。
1 | private static void Main() |
发现是对一段 data 进行异或,但是数据在哪里不知道,用附加进程进行动调 (然后发现是个小黑子程序)
调试到 for 循环结束以后查看 data 的内存
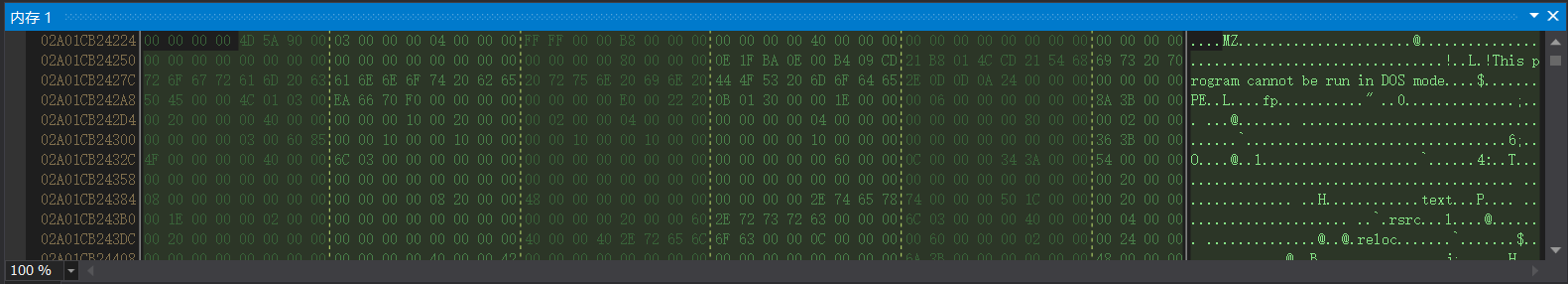
发现是 MZ 开头,显然是一个 PE 文件,我们把它 dump 下来
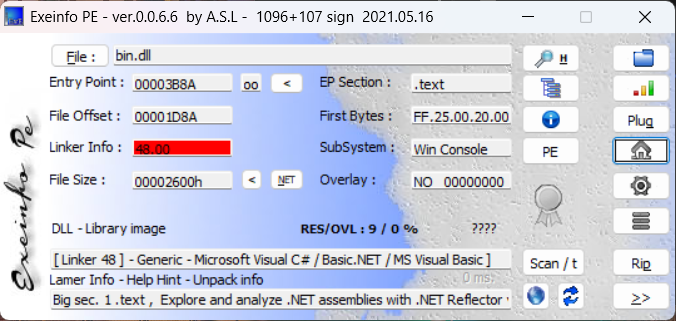
发现还是用 C# 写的 .net 文件,继续用 dnspy 反编译,里面有一个巨大的 if 里面有个 array 数组
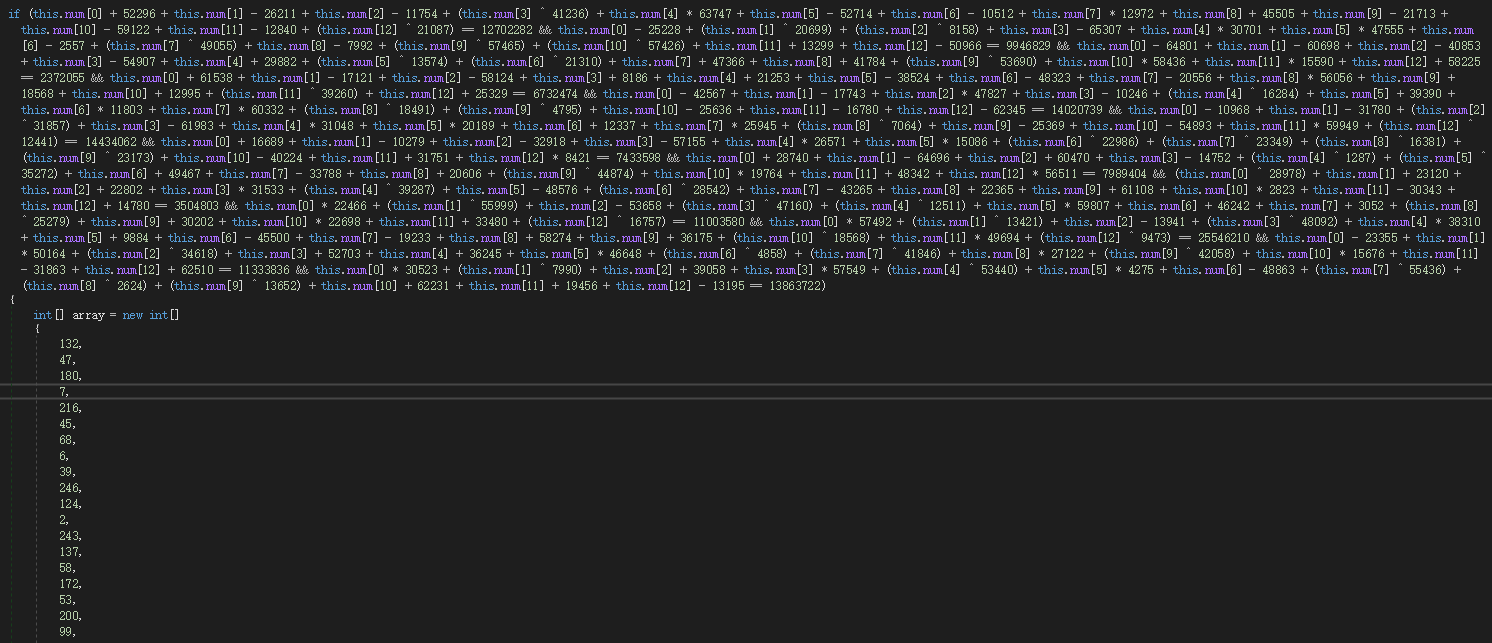
我们需要知道 num 数组里到底有些啥,直接上 z3即可。
1 | from z3 import * |
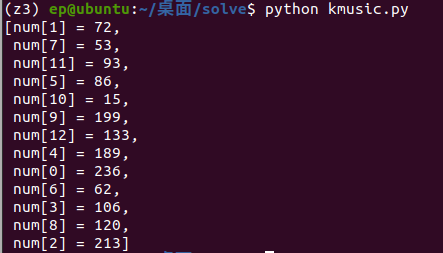
然后执行下面的代码
1 | num = [0 for i in range(13)] |
得到 hgame{z3_1s_very_u5eful_1n_rever5e_engin3ering}
cpp
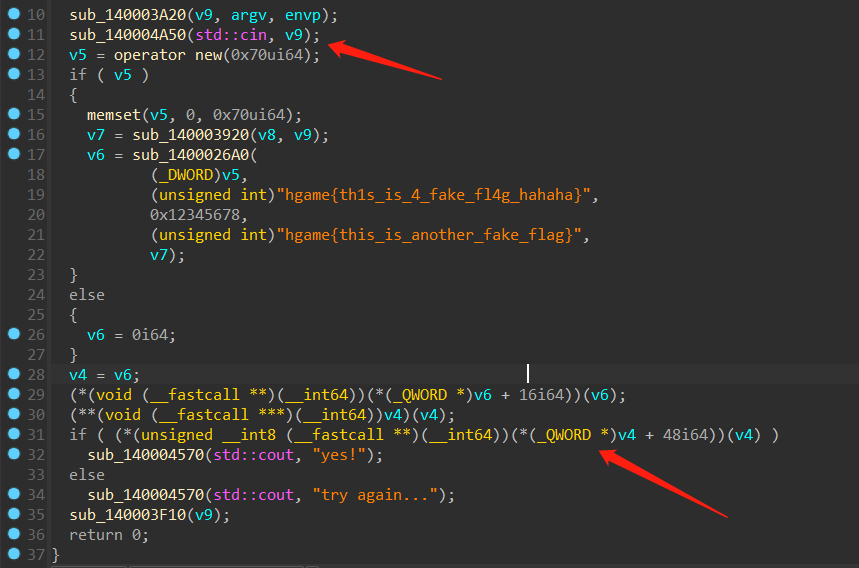
函数调用反编译出来是 fastcall, 没办法静态找到调用的是哪个函数,直接动调就行。
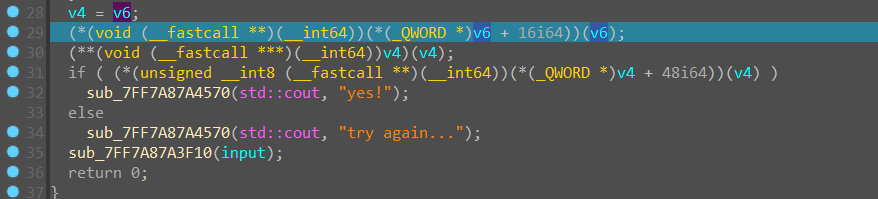
跳到 v6 这里的 时候,结合下面的函数调用,很像一个密钥的初始化函数,但是不知道是啥加密算法,但是无所谓,我们接着跟踪代码对输入的 flag 进行了什么操作,进入第二个调用
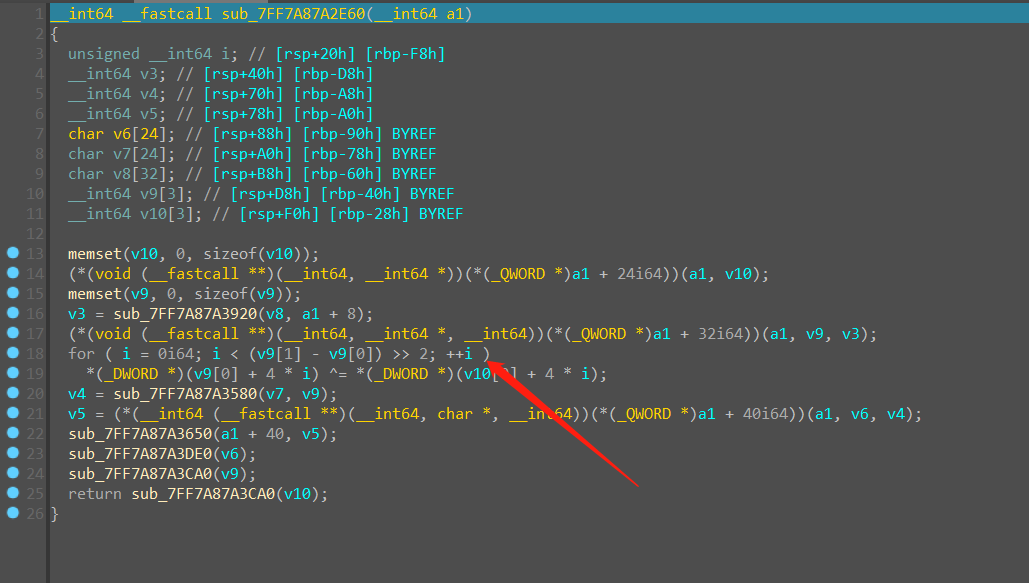
动调到箭头指向的这一步,发现在异或之前,flag 都没有改变,于是考虑直接把与flag异或的值给 dump 出来,注意这里应该是改了大小端序的。
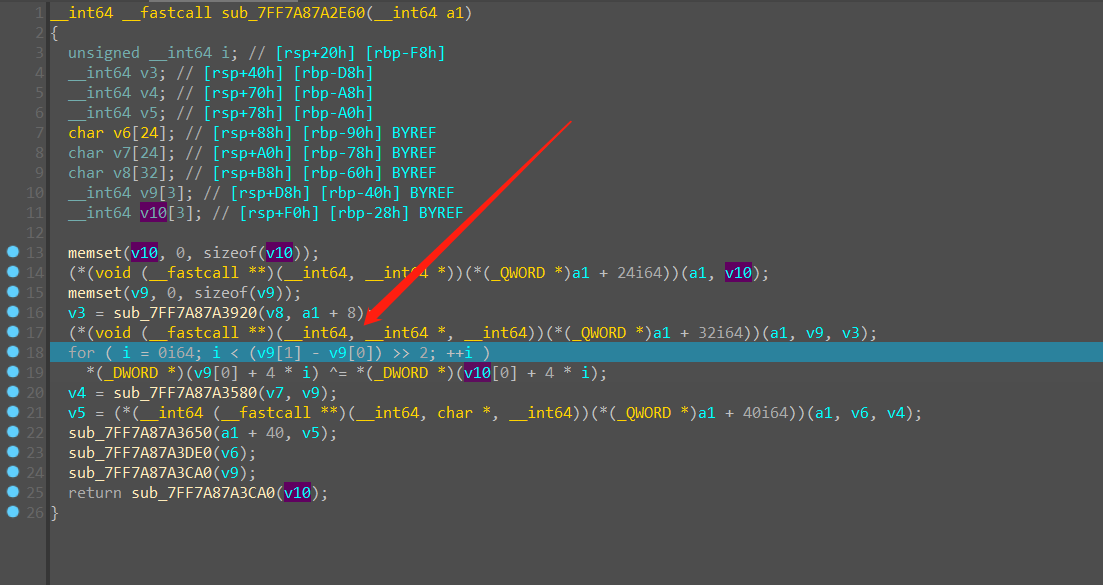
后面进入 check 函数
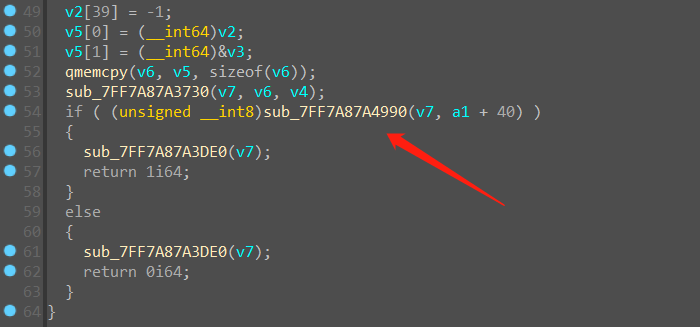
跟踪进入函数sub_7FF7A87A4990,发现是memcpy
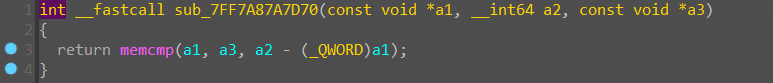
找到相对应的参数,可以 dump 出密文
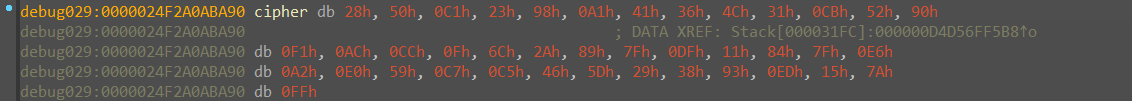
写出 exp
1 |
|
运行得到 hgame{Cpp_1s_much_m0r3_dlff1cult_th4n_C}
shellcode
golang逆向,一眼看见 base64_decode 函数,考虑直接把解码后的 shellcode dump出来
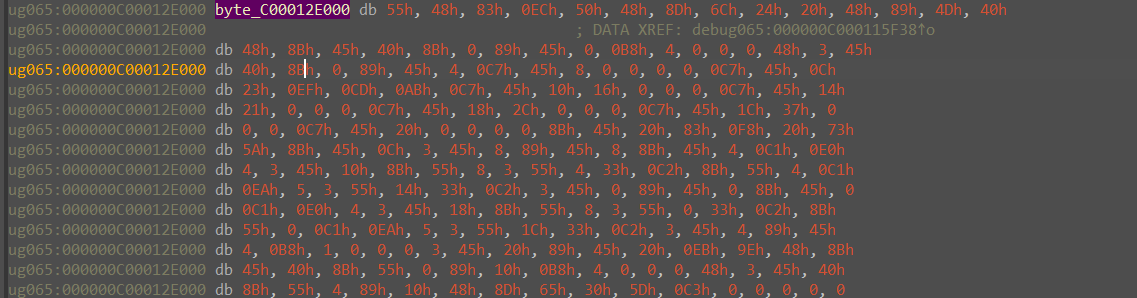
然后贴到 010editor 里用 ida64 打开,创建函数反编译以后发现是个 TEA ,密钥是常数,密文应该就是 flag.enc
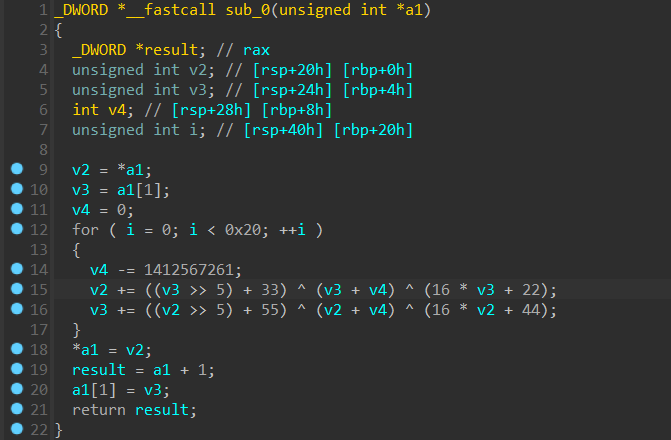
写出 exp
1 |
|
得到 hgame{th1s_1s_th3_tutu's_h0mew0rk}


