BeginCTF2024-re-wp
红白机
6502汇编,直接找一个在线网站编译运行一下即可
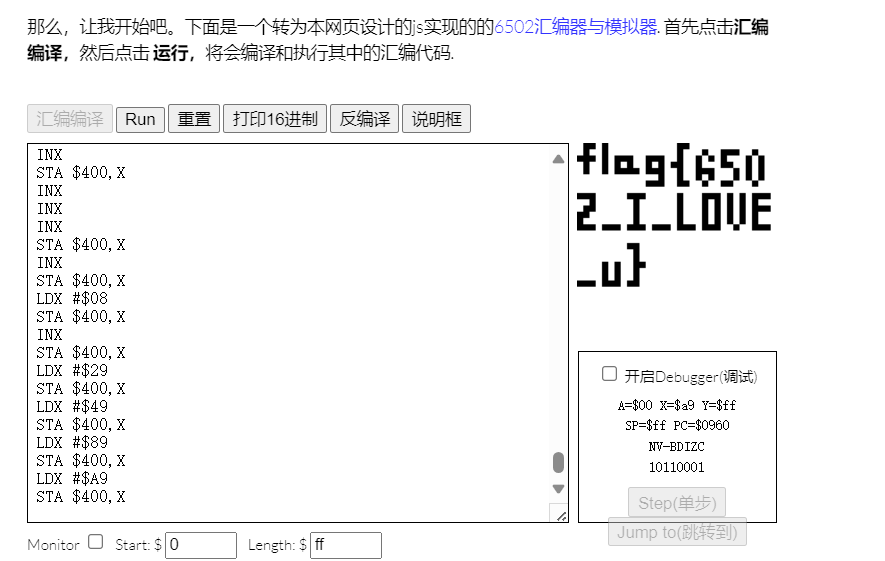
Xor
upx -d去壳,然后一堆轮密钥异或,细致一些就可以
1 |
|
俄语学习
RC4,但是逆完了发现根本不要RC4,因为明文和密文都用了相同的轮密钥进行了加密,直接偏移即可
1 |
|
Ezpython
用pyinstxtractor解包,再对ezpython.pyc进行反编译,发现缺少了以下函数
1 | from gmssl import sm4 |
再对 sm4.pyc,secret.pyc进行反编译
密钥和密文是
1 | key = 'BeginCTFBeginCTF' |
直接 SM4 解密是错的,通过反编译的sm4.py发现有魔改,对密钥进行了异或 37 的操作
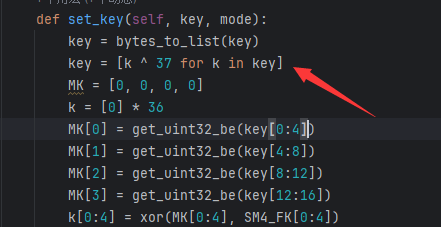
异或密钥以后扔cyberchef解密
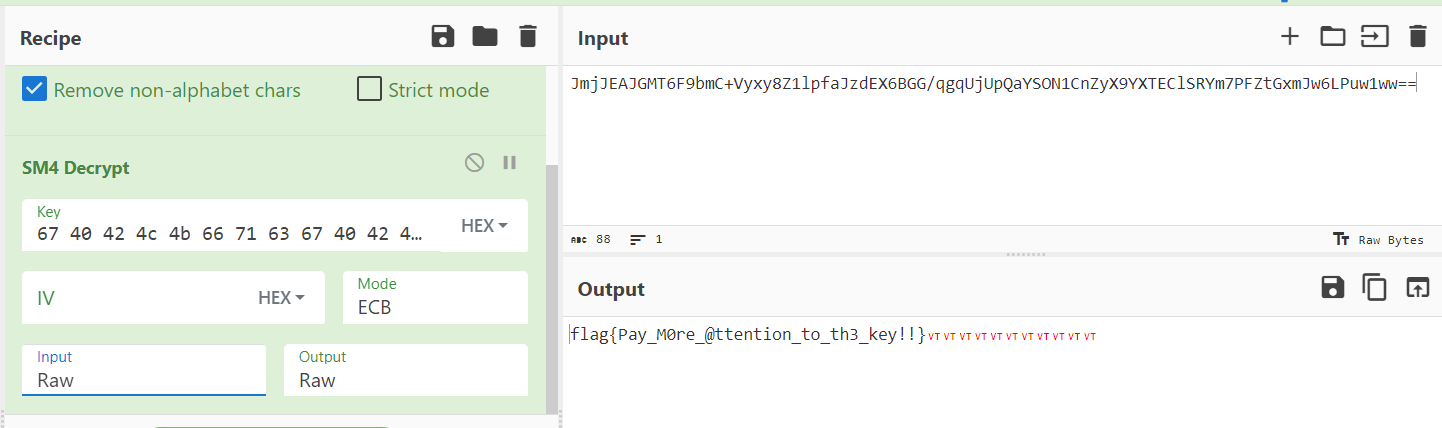
Superguessor
有混淆和反调试,如果kernel32_IsDebuggerPresent返回结果为1异或0x44,为0异或0x33
1 |
|
real checkin xor
1 | secret = [7, 31, 56, 25, 23, 15, 91, 21, 49, 15, 33, 88, 26, 48, 60, 58, 4, 86, 36, 64, 23, 54, 63, 0, 54, 22, 6, 55, 59, 38, 108, 39, 45, 23, 102, 27, 11, 56, 32, 0, 82, 24] |
出题人的密码是什么
花指令,nop 掉即可,然后交叉引用找到加密逻辑,通过改标志位绕过反调试
此外还有一个时间反调试

逻辑如下
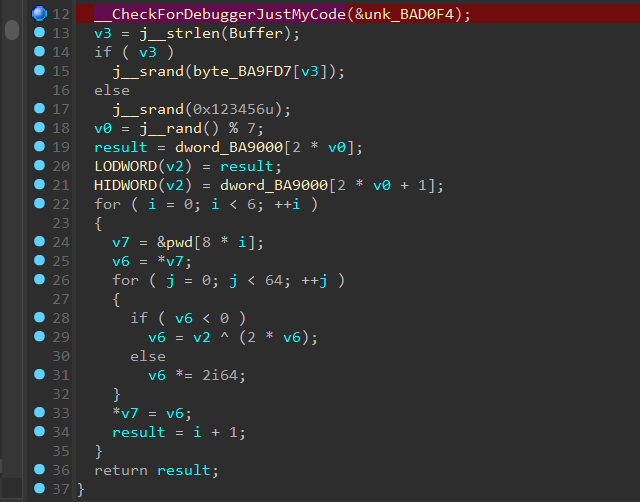
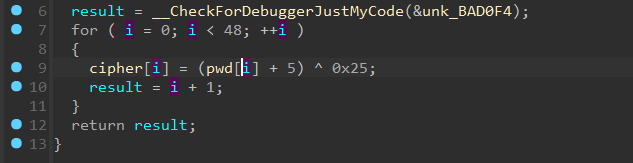
直接逆向,先异或,然后上面那个算法是判断最高位是不是1,然后对低位进行异或,那么我们就可以根据最低位来求出最高位
1 | enc = bytes.fromhex('B4BBD8EBD06EABCA658E4BE94DD44AF37D29C2F99589A4859DCDDF77FD45CB5D7DFD934BBCF67CF32442F5D2DDE356AE') |
arc
解包后反编译,然后是一大坨 list
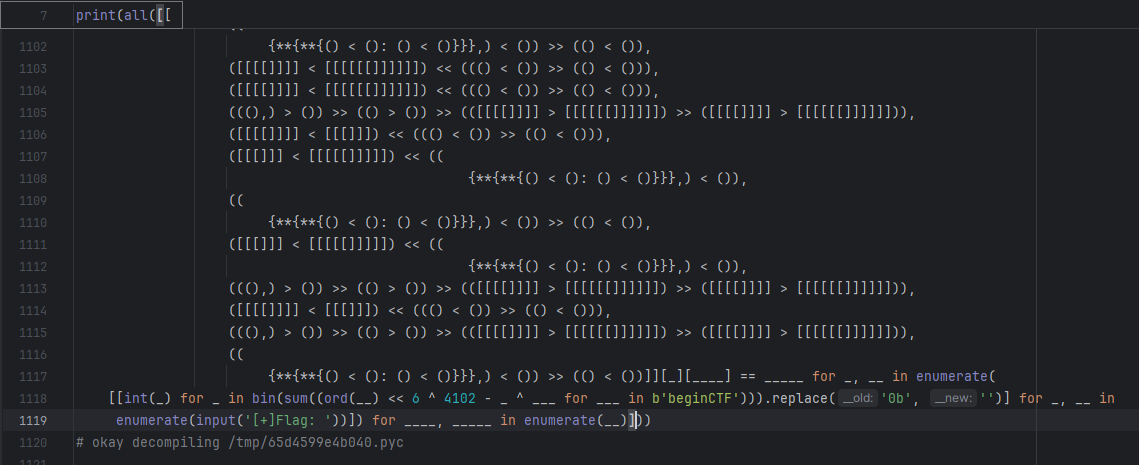
其实就是通过大于小于符号和位运算嵌套最后的结果就是1或者0
所以整体的结构就是 list[list[int]][i][j] == data
直接爆破
1 | enc = list[list[int]] |
goforfun
先用 go_parser 恢复符号表,然后动调查看逻辑
一个奇怪的 rc4,但是不用管流程,直接dump最后的异或流密钥即可
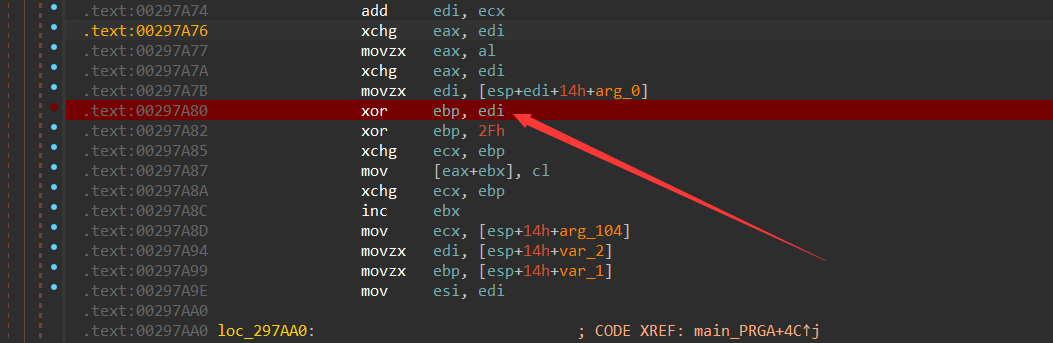
然后是一个大整数的操作,就是把一个数组先用 BYTE 转化成一个大整数,然后再每次取模64,再除以64,得到一个最大不超过64的数组,再以这个数组为索引进行单表代换最后比对,直接逆即可
1 | key = [0x84, 0xe, 0x79, 0xc1, 0x29, 0x3d, 0xe7, 0x86, 0x93, 0xf4, 0xb4, 0x66, 0x64, 0xaf, 0x19, 0x97, 0x85, 0x7, 0xe6, 0x4a, 0xc8, 0x3, 0x37] |
Not main
veh 异常处理,运行main函数前先利用 initterm 注册了一个 VEH 处理器,在main函数之前执行了一个构造函数
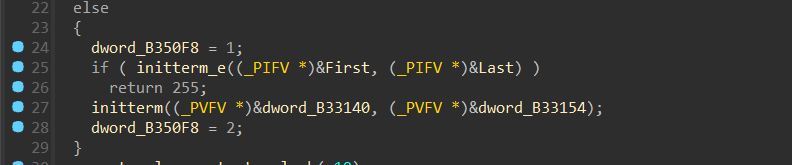
并进行了一处反调试
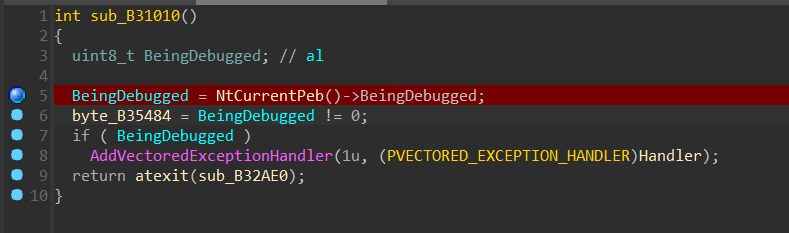
sub_B32AE0是注册的析构函数,patch掉以后走完main流程会进入析构函数
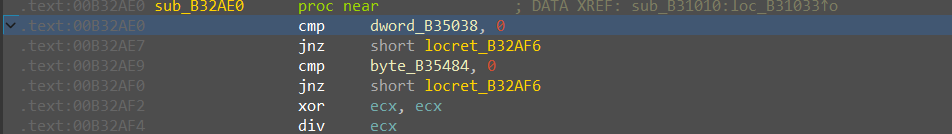
发现是对之前的BeingDebugged进行检测,通过以后触发除零异常再进入 Handler 函数进行xxtea加密。
也就是走了一次main函数里的 tea 加密又走了一次 handler 里的 xxtea,解密即可
1 |
|
ezvm
虚拟机,opcode如下
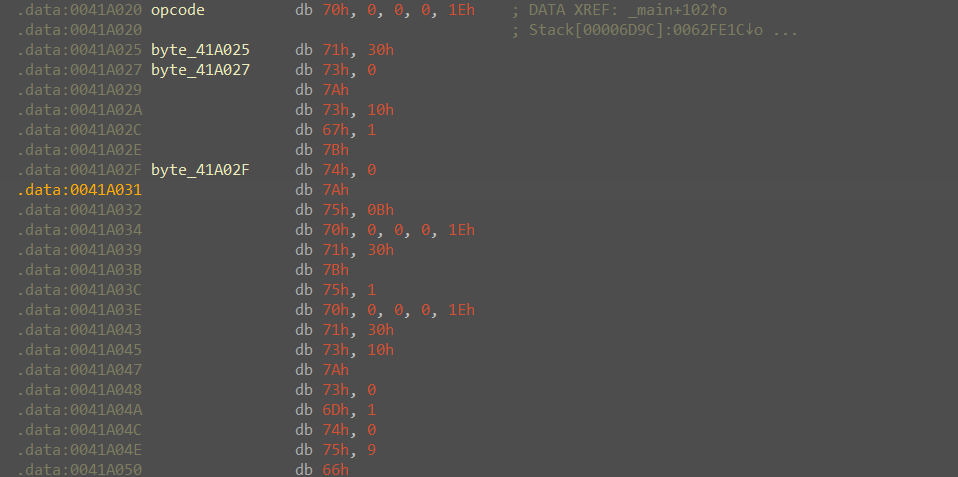
然后就是摘棉花反汇编
1 | data = [0xC7, 0x0B, 0xDB, 0x0C, 0xE5, 0x08, 0xAD, 0xDE, 0xAF, 0xCD, 0x67, 0xBF, 0x1F, 0xBF, 0x1E, 0x68, 0xFE, 0x25, 0xFD, 0x6F, 0x08, 0x50, 0xCD, 0x15, 0xB0, 0x21, 0x8B, 0x3E, 0xFD, 0x73, 0xED, 0x90] |


